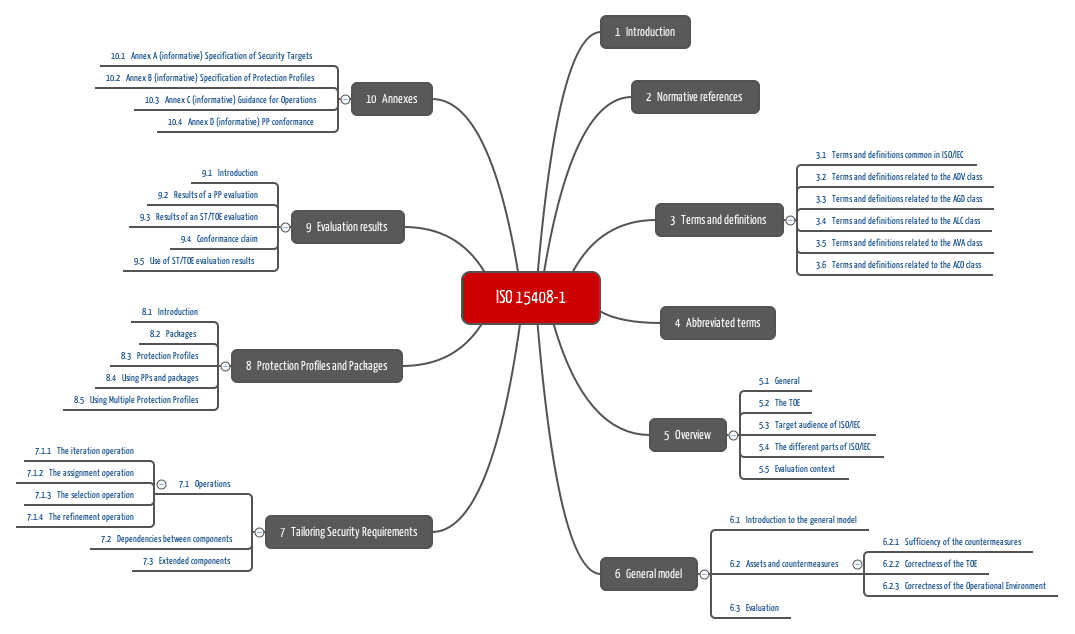
Iso 15408
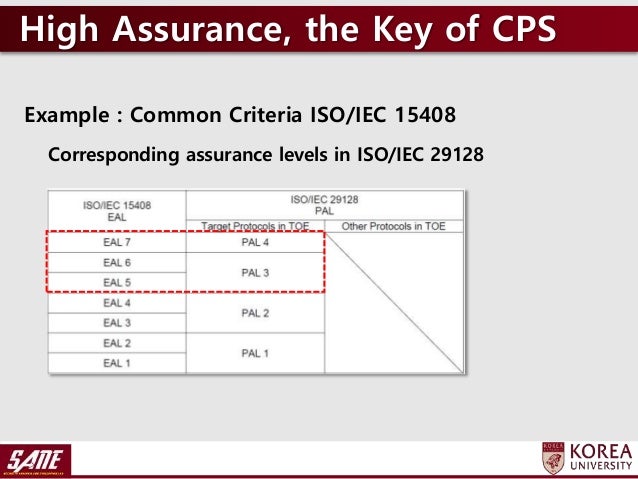
Standard ISO/IEC , CC v31 Release 4 More recently, PP authors are including cryptographic requirements for CC evaluations that would typically be covered by FIPS evaluations, broadening the bounds of the CC through schemespecific interpretations.
Iso 15408. The audience for this part of ISO/IEC includes consumers, developers, and evaluators of secure IT products ISO/IEC , Clause 5 provides additional information on the target audience of ISO/IEC , and on the use of ISO/IEC by the groups that comprise the target audience. ISO/IEC Common Criteria Common Criteria (CC) is an international standard that ensures that IT products and systems are securely designed and constructed Since the 1980s, countries in Europe and America had been using their own security standards to evaluate products for military and government. An ISO/IEC certificate would be a good addition to let the customers know that their confidential information is in good hands Evaluation ST/TOE is the evaluation that is discussed in the general model of ISO/IEC This evaluation is carried out in two steps The first step or part of the evaluation is called the ST evaluation.
Standard NumberCSA ISO/IEC 1963 Standard NameIT security techniquesCompetence requirements for information security testers and evaluators Part 3Knowledge, skills and effectiveness requirements for ISO/IEC evaluators Size535M FormatPDF Introduction1 Scope This document provides the specialized requirements to demonstrate. ISO/IEC 1540 was prepared by Joint Technical Committee ISO/IEC JTC 1, Information technology, Subcommittee SC 27, IT Security techniques The identical text of ISO/IEC is published by the Common Criteria Project Sponsoring Organisations as Common Criteria for Information Technology Security Evaluation. A travs del cumplimiento de siete niveles de evaluacin (EAL1 EAL7), garantiza seguridad en la operacin controlada de una TIC.
The Common Criterial is divided in to three main parts (“ISO/IEC Standard — ENISA”) Part 1 Introduction and general model () This is a general overview of the standards The user can use this part as a start to understand and implement the overall criteria for information security. ISO/IEC is useful as a guide for the development, evaluation and/or procurement of IT products with security functionality ISO/IEC is intentionally flexible, enabling a range of evaluation methods to be applied to a range of security properties of a range of IT products Therefore users of the standard are cautioned to exercise care. ISO is the international standard for certifying computer security You could say that ISO , also called the Common Criteria, provides the basic recipe for cooking up a secure IT product or system This is the framework by which organizations show that their product specs, the implementation, and security evaluations have all been.
Common Criteria (ISO/IEC ) SecurePay Platform 48 evaluated for common criteria EAL2 The Evaluation Assurance Level (EAL1 through EAL7) of an IT product or system is a numerical grade assigned following the completion of a Common Criteria security evaluation, an international standard in effect since 1999 The increasing assurance levels reflect added assurance requirements that must be. What is Common Criteria?. The various operations by which the functional and assurance components given in ISO/IEC 1540 and ISO/IEC 1540 may be tailored through the use of permitted operations;.
About ISO EAL6 and the Common Criteria The Common Criteria for Information Technology Security Evaluation (CC) is an international standard (ISO/IEC ) for computer security certification. ISO/IEC defines the content and presentation of the assurance requirements in the form of assurance classes, families and components and provides guidance on the organization of new assurance requirements The assurance components within the assurance families are presented in a hierarchical order. ISO/IEC defines two forms for expressing IT security functional and assurance requirements The protection profile (PP) construct allows creation of generalized reusable sets of these security requirements.
ISO/IEC gives guidelines for the specification of Security Targets (ST) and provides a description of the organization of components throughout the model General information about the evaluation methodology is given in ISO/IEC and the scope of evaluation schemes is provided. ISO/IEC 154 08 Evaluation Criteria for Information Technology Security represents the ou tcome o f series of efforts to develop cr iteria for evaluation of IT Security that are broadly useful within th e international comm unity The secur ity assurance that user required can come from various method ;. Ricoh Products Certified with Common Criteria (ISO/IEC ) To ensure that our devices have been designed and implemented in conformance with specific security standards, many Ricoh products are indepently tested and verified The products listed on this page have received Common Criteria certification.
El estndar ISO/IEC es uno de los ms relevantes a nivel mundial en seguridad informtica;. ISO is a specific standard developed for Information Technology Security Techniques It establishes the general concepts and principles of IT security evaluation and specifies the general model of evaluation given by various parts of ISO/IEC which in its entirety is meant to be used as the basis for evaluation of security properties. Guidance for the application of ISO/IEC in order to develop evaluation methods (EM.
AS ISO Financial services Secure cryptographic devices (retail) Concepts, requirements and evaluation methods ISO/IEC 1540 08(R14). These solutions meet the most stringent cybersecurity standard ISO , the Common Criteria (ISO ), and can increase original equipment manufacturer (OEM) reliability to % GuardKnox's Patented Cybersecuity Technologies for Vehicles Earn Acclaim from Frost and Sullivan. ISO/IEC defines the content and presentation of the security functional requirements to be assessed in a security evaluation using ISO/IEC It contains a comprehensive catalogue of predefined security functional components that will meet most common security needs of the marketplace.
ISO/IEC defines the content and presentation of the assurance requirements in the form of assurance classes, families and components and provides guidance on the organization of new assurance requirements The assurance components within the assurance families are presented in a hierarchical order. Regular Price $325 Sale Price $ COLOR GALLERY Sale COLOR. The ISO EAL6 certificate is an international standard for IT product security certification The certification received by ASE was issued by the German Government’s Federal Office for IT.
ISO/IEC is useful as a guide for the development of products or systems with IT security functions and for the procurement of commercial products and systems with such functions During evaluation, such an IT product or system is known as a Target of Evaluation (TOE). In my opinion the ISO/IEC or the Common Criteria is a comprehensive standard that can guide all security experts better understand their security needs and implement strategies that would ensure the safety and security of their information systems. This part of ISO/IEC defines the required structure and content of security functional components for the purpose of security evaluation General Product Information (Show below) (Hide below).
Nonbinding ISO standard Affected sectors Generic The standard can be implemented in any sector confronted by the need to test the security of IT products and systems Relevant provision(s) The standard is made up of three parts a) Part 1, Introduction and general model, is the introduction to ISO/IEC. ISO/IEC gives guidelines for the specification of Security Targets (ST) and provides a description of the organization of components throughout the model General information about the evaluation methodology is given in ISO/IEC and the scope of evaluation schemes is provided. The Common Criteria ISO/IEC The Insight, Some Thoughts, Questions and Issues by Ariffuddin Aizuddin October 1, 01 This paper provides an overview of an international effort called Common Criteria (CC), an IT Security evaluation methodology, developed to define and facilitate consistent evaluations of security products and systems, fostering international recognition and trust in.
Níves de garantia ISO (Commom Criteria)EAL1 43 CON – A3 10 Níves de garantia ISO (Commom Criteria)EAL1 44 CON – A3 11 Níves de garantia ISO (Commom Criteria) 45 CON – A3 12. ISO/IEC defines the assurance requirements of the evaluation criteria It includes the evaluation assurance levels that define a scale for measuring assurance for component targets of evaluation (TOEs), the composed assurance packages that define a scale for measuring assurance for composed TOEs, the individual assurance components from which the assurance levels and packages are. ISO/IEC gives guidelines for the specification of Security Targets (ST) and provides a description of the organization of components throughout the model General information about the evaluation methodology is given in ISO/IEC and the scope of evaluation schemes is provided.
ISO/IEC establishes the general concepts and principles of IT security evaluation and specifies the general model of evaluation given by various parts of ISO/IEC which in its entirety is meant to be used as the basis for evaluation of security properties of IT products. ISO/IEC (E) PDF disclaimer This PDF file may contain embedded typefaces In accordance with Adobe's licensing policy, this file may be printed or viewed but. Ie, if we have two products, is the one which has a higher.
ISO/IEC Acquisition Status Fuji Xerox has acquired ISO/IEC * for below products *ISO/IEC provides independent, objective, validation of the reliability, quality, and trustworthiness of IT products It is the only international standard that customers can rely on to help them make informed decisions about their IT purchases. Regular Price $325 Sale Price $ COLOR GALLERY Sale COLOR. Iso Satakieli BRAND Marimekko COLLECTION Marimekko III SALE Type Wallpaper Stock only 2 rolls left Add to wishlist Add to wishlist Humanity and nature converge in pure poetry SHOP MORE SALE ITEMS!.
Iso Satakieli BRAND Marimekko COLLECTION Marimekko III SALE Type Wallpaper Stock only 2 rolls left Add to wishlist Add to wishlist Humanity and nature converge in pure poetry SHOP MORE SALE ITEMS!. Regarding Common Criteria, it is also an ISO standard (ISO ), although ISO is related to the certification of companies, while Common Criteria (ISO ) is related to the certification of products. Purchase your copy of BS EN as a PDF download or hard copy directly from the official BSI Shop All BSI British Standards available online in electronic and print formats BS EN Solid recovered fuels.
Common Criteria (ISO/IEC *1) certification Common Criteria(CC) refers to international criteria for evaluation of information technology security It is used for evaluating whether security functions are appropriately developed for IT products. ISO/IEC defines the content and presentation of the assurance requirements in the form of assurance classes, families and components and provides guidance on the organization of new assurance requirements The assurance components within the assurance families are presented in a hierarchical order. Common Criteria (ISO/IEC ) is an international evaluation standard of information security This internationally recognized standard has been created to evaluate if security functions of IT products are appropriately designed and implemented in order to sufficiently counter threats.
A travs del cumplimiento de siete niveles de evaluacin (EAL1 EAL7), garantiza seguridad en la operacin controlada de una TIC. El estndar ISO/IEC es uno de los ms relevantes a nivel mundial en seguridad informtica;. In the introduction part of ISO/IEC the further clauses of the ISO standard are introduce in brief It defines the general concepts and principles of IT security evaluation and presents a general model of evaluation.
The Common Criteria for Information Technology Security Evaluation (referred to as Common Criteria or CC) is an international standard (ISO / IEC ) for computer security certification It is currently in version 31 revision 5. I have a question about ISO/IEC standard I want know if the level of evaluation is higher we can conclude that a product is safer?. The Common Criteria for Information Technology Security Evaluation (Common Criteria or CC) is an international standard (ISO / IEC ) for IT product security certification It is a framework that provides criteria for independent, scalable and globally recognized security inspections for IT products.
Common Criteria (ISO/IEC ) Certification Common Criteria (ISO/IEC ) is an international evaluation standard of information security This internationally recognized standard has been created to evaluate if security functions of IT products are appropriately designed and implemented in order to sufficiently counter threats. The Common Criteria for Information Technology Security Evaluation (CC), and the companion Common Methodology for Information Technology Security Evaluation (CEM) are the technical basis for an international agreement, the Common Criteria Recognition Arrangement (CCRA), which ensures that Products can be evaluated by competent and independent licensed laboratories so as to determine the. I have a question about ISO/IEC standard I want know if the level of evaluation is higher we can conclude that a product is safer?.
Requirements specified in the ISO/IEC series, ISO/IEC and ISO/IEC also allow that more specific Evaluation Activities (EAs) may be derived for use in particular evaluation contexts Specification of such Evaluation Activities is already occurring amongst practitioners and this creates a. The ISO/IEC Evaluation Criteria For IT Security Package defines the security functional requirements and assurance components while providing general concepts and principles of IT security evaluation. Standard ISO/IEC , CC v31 Release 4 More recently, PP authors are including cryptographic requirements for CC evaluations that would typically be covered by FIPS evaluations, broadening the bounds of the CC through schemespecific interpretations.
General information about the evaluation methods given in ISO/IEC ;. ISO/IEC is useful as a guide for the development of products or systems with IT security functions and for the procurement of commercial products and systems with such functions During evaluation, such an IT product or system is known as a Target of Evaluation (TOE) Such TOEs include, for example, operating. — supplementary activities to methodology specified in ISO/IEC for SAR Classes of ISO/IEC 1540 This document introduces the general framework for the security evaluation of biometric systems, including extended security functional components, and supplementary activities to methodology, which is additional evaluation activities and guidance/recommendations for an evaluator to handle those activities.
Formalized as ISO/IEC , the Common Criteria (CC) defines a hierarchical framework of security concepts and terminology The CC also defines the Protection Profile (PP) construct which is a product category specific but product agnostic requirements template. ISO/IEC XX, Information security, cybersecurity and privacy protection — Evaluation criteria for IT security — Part 1 Introduction and general model ISO/IEC 1540XX, Information security, cybersecurity and privacy protection — Evaluation criteria for IT security — Part 2 Security functional components. ISO/IEC international standard However, these governmental organisations retain the right to use, copy, distribute, translate or modify CC 31 as they see fit.
Ie, if we have two products, is the one which has a higher. ISO is a specific standard developed for Information Technology Security Techniques. The Common Criteria for Information Technology Security Evaluation (referred to as Common Criteria or CC) is an international standard (ISO/IEC ) for computer security certification It is currently in version 31 revision 5 Common Criteria is a framework in which computer system users can specify their security functional and assurance requirements (SFRs and SARs respectively) in a.
本稿では,iso/iec の概要,制度動向およびnecの 取り組みについて解説します。 2.iso/iec の概要 21 iso/iec とは it製品・システムのセキュリティ機能が適切に設計され, その設計が正しく実装されているかどうかを客観的に評価. ISO/IEC Common Criteria Common Criteria (CC) is an international standard that ensures that IT products and systems are securely designed and constructed Since the 1980s, countries in Europe and America had been using their own security standards to evaluate products for military and government. Formalized as ISO/IEC , the Common Criteria (CC) defines a hierarchical framework of security concepts and terminology The CC also defines the Protection Profile (PP) construct which is a product category specific but product agnostic requirements template This allows prospective consumers, developers and regulatory groups to create standardized sets of security.
ENISO/IEC is a companion document to the “Evaluation criteria for IT security”, ISO/IEC This International Standard defines the minimum actions to be performed by an evaluator in order to conduct an ISO/IEC evaluation, using the criteria and evaluation evidence defined in ISO/IEC. — supplementary activities to methodology specified in ISO/IEC for SAR Classes of ISO/IEC 1540 This document introduces the general framework for the security evaluation of biometric systems, including extended security functional components, and supplementary activities to methodology, which is additional evaluation activities and guidance/recommendations for an evaluator to handle those activities.

O Z Dst Iso Iec 1 16 In English Download Pdf Gostperevod Com

Cybersecurity And Medical Devices Are The Iso Iec 2 2 Technical Controls Up To The Challenge Sciencedirect

Common Criteria Iso Iec Securepay Sdn Bhd
Iso 15408 のギャラリー
Nou Intuit Lekciya Sovremennye Standarty V Oblasti Informacionnoj Bezopasnosti Ispolzuyushie Koncepciyu Upravlenie Riskami
Www Jtsec Es Papers Technical Report Patch Management Pdf

Active And Personalized Services In An Information Security Engineering Cloud Based On Iso Iec Springerprofessional De

En Iso Iec 2 Information Technology Security Techniques Evaluation Criteria For It Security Part 2 Security Functional Components Iso Iec 2 08

Iso Iec 1 09 Iec Normen Vde Verlag

Iso Iec Security Concepts 17 Download Scientific Diagram

Figure 3 From A Supporting Tool For Creating And Maintaining Security Targets According To Iso Iec Semantic Scholar

Uniform Standards Iso Security Practices Commentary Of Government Procurement 06 Isbn Japanese Import Amazon Com Books

Security Standards
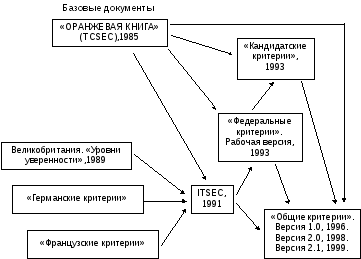
3 7 Mezhdunarodnyj Standart Iso Obshie Kriterii

Supporting Verification And Validation Of Security Targets With Iso Iec Semantic Scholar

Multiapp V2 Pace Sac Common Criteria Iso Manualzz

St Rk Iso Iec 3 17
Media Ccc De The New Eu Cybersecurity Act
Www Commoncriteriaportal Org Iccc 9iccc Pdf T01 Pdf

Iso Formation Of The Common Criteria Standard

Seguranca De Aplicacoes Iso Diego Maia E Tiago Motta Youtube
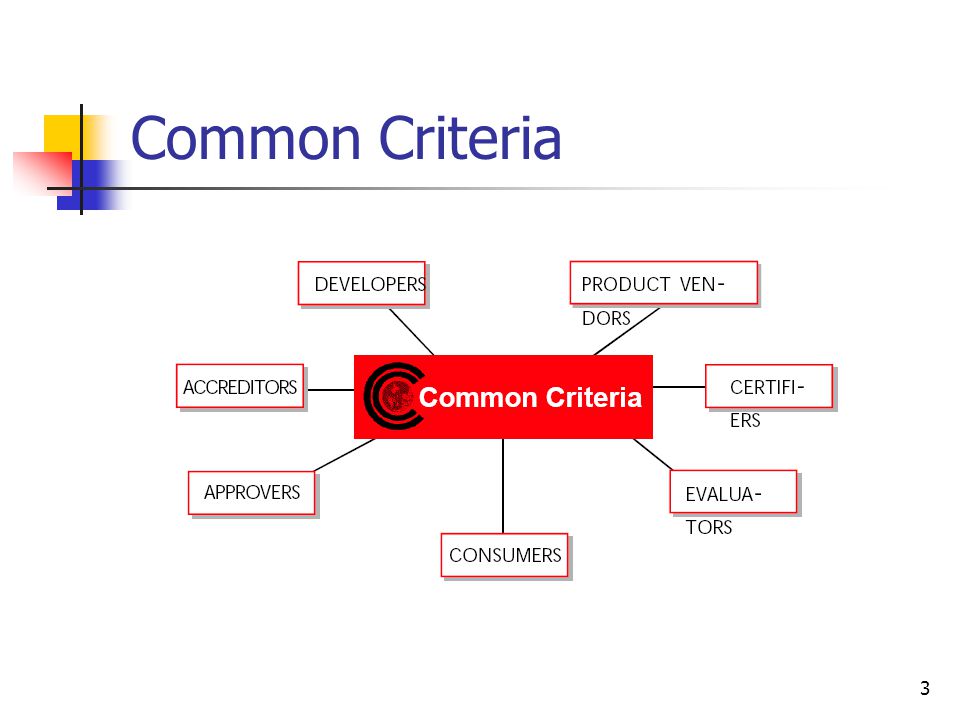
1 Common Criteria Ravi Sandhu 2 Common Criteria International Unification Cc V2 1 Is Iso Flexibility Separation Of Functional Requirements Assurance Ppt Download

Knowledge In Is It Processes And Standards Advisor Dr Celeste

Common Criteria For It Security Evaluation Cc Iso Iec

Auditoria Y Seguridad De Sistemas De Informacion Iso Iec Common Criteria I
Www Midshire Co Uk Wp Content Uploads 12 10 Iso It Security Certification Factsheet Pdf

Supporting Verification And Validation Of Security Targets With Iso Iec Semantic Scholar

Cyber Security Threats In Healthcare Vde Medical Devices And Software

Sist En Iso Iec 3 Information Technology Security Techniques Evaluation Criteria For It Security Part 3 Security Assurance Components Iso Iec 3 08

Ppt Data Security On Ta Triumph Adler Syncontrol Systems System Support Powerpoint Presentation Id

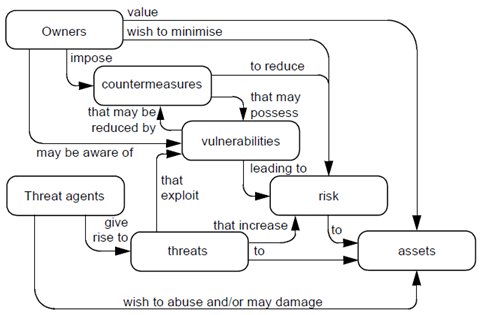
Risk Context Source Iso Iec 1 Common Criteria Download Scientific Diagram

An Iso Iec 2 Compliant Security Auditing System With Blockchain Technology Semantic Scholar

What Is Iso 1 Nobel Cert Universal Training Iso Ce
Iso Iec It Sicherheit Von Medizin Produkten Bewerten
Iso Iec Common Criteria Iso Security Solutions Page 1
Security Guideline Tool For Home Users Based On International Standards Emerald Insight
Cb16 Using The Cgc S Fully Automated Vulnerability Detection Tools

Protection Profile Contents According To The Standard Iso Iec Download Scientific Diagram
2

Figure 1 From A Supporting Tool For Creating And Maintaining Security Targets According To Iso Iec Semantic Scholar
Dr Rachid Zagrouba Risk Management Iso

Iso Ortak Kriterler Standardi Danismanligi Proxy Egitim Ve Danismanlik
.jpg)
Incits Iso Iec 3 08 R18 Information Technology Security Techniques Evaluation Criteria For It Security Part 3 Security Assurance Components

Iso Iec Tr 004 15 Iec Normen Vde Verlag

Pdf An Approach For Software Security Evaluation Based On Iso Iec In The Isms Implementation Journal Of Computer Science Ijcsis Academia Edu

Saho 商合行

Din En Iso Iec 1 Draft

En Iso Iec 3 Information Technology Security Techniques Evaluation Criteria For It Security Part 3 Security Assurance Components Iso Iec 3 08

Safelayer Obtains Cc Eal4 Iso Iec Certification For Version 4 0 Of Its Keyone Platform Safelayer
Ec Europa Eu Transport Sites Transport Files Themes Its Road Action Plan Doc 10 03 18 Smart Ticketing Pdf

Ppt 國際標準 Iso Iec 的介紹powerpoint Presentation Id

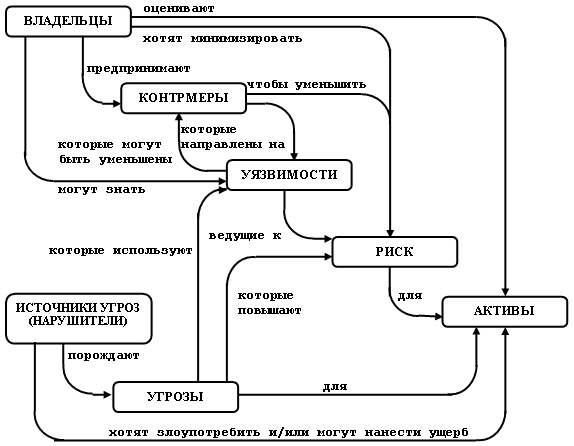
Mezhdunarodnyj Standart Iso Obshie Kriterii Audit Informacionnoj Bezopasnosti

Iso Iec How To Structure And Explain In What Way Can We Redefine The Criteria Of Choice Of Iso Iec Requirements Hybrid It

Iso A Complete Guide Edition E Book Gerardus Blokdyk Storytel

Smart Grid Cybersecurity Standards Incibe Cert

Iso Ortak Kriterler Poster By Sealcert Issuu

The Elements Relevant To It Risks And Their Relationships According To Download Scientific Diagram

Epson High Speed Linehead Inkjet Multifunction Printers Receive Iso Iec It Security Certification July 23 18 Newsroom Epson
Www Law Kuleuven Be Citip En Docs Hot News Conferences Antonio Kung Pdf

Iso Ts 09 En Electronic Fee Collection Guidelines For Security Protection Profiles

Cc Iso の基礎

Security Target Contents According To Iso Download Scientific Diagram
Ieeexplore Ieee Org Iel7 Pdf

Pecb Iso Information Technology Security Techniques Application Security

Csa Iso Iec 196 3 Free Standards Download

Iso Iec Ts 18 Iec Normen Vde Verlag

Iso Satakieli

Common Criteria Iso Iec Securepay Sdn Bhd
Gobierno De La Ciberseguridad Iso Y El Dni E Pp Para El Desarrollo De Aplicaciones Parte I

Iso Iec Cc Kompass Der It Sicherheitsstandards

Iso Iec 1 09
2

Risk Context Source Iso Iec 1 Common Criteria Download Scientific Diagram
Security Guideline Tool For Home Users Based On International Standards Emerald Insight

Ppt Common Criteria Powerpoint Presentation Free Download Id

Iso Iec 1 09 En Information Technology Security Techniques Evaluation Criteria For It Security Part 1 Introduction And General Model

Iso Common Criteria

News Samsung Research
2

Instituto Nacional De Normalizacion Iso Iec 1 09

Iso Iec Common Criteria ارزیابی امنیتی محصولات فناوری اطلاعات Pdf Document
Http Www Lanoms Org 05 Anaiscd 05 P2 5 Pdf
Iso Iec It Sicherheit Von Medizin Produkten Bewerten

The Common Criteria Cisa

Common Criteria Services Wo Tuv Rheinland
Iso 1 05 Certificate Service In Silver Coin Apartment Vadodara Shahi Enterprises Id

Iso Iec 1 Ipsec Pl

Norm Csn Iso Iec 1 36 97 1 2 13

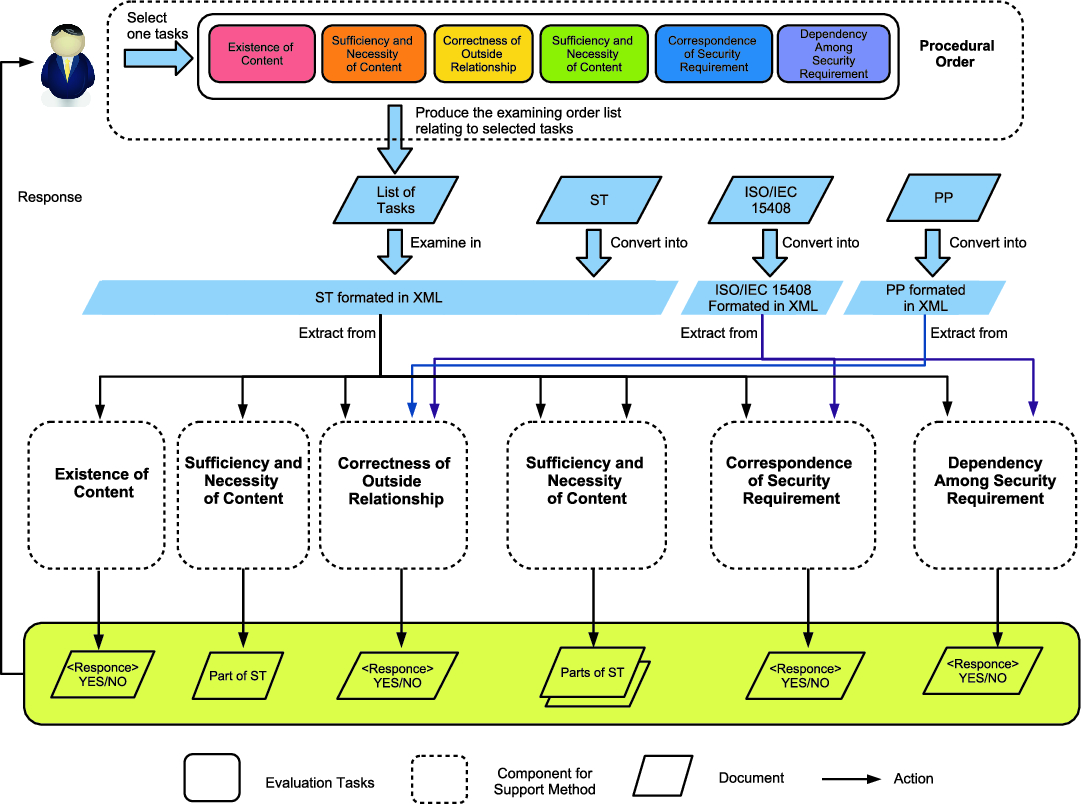
Feasibility Study Workshop For It Security Evaluation Cc Iso Iec And Certification
2
Ipsj Ixsq Nii Ac Jp Ej Index Php Action Pages View Main Active Action Repository Action Common Download Item Id Item No 1 Attribute Id 1 File No 1 Page Id 13 Block Id 8
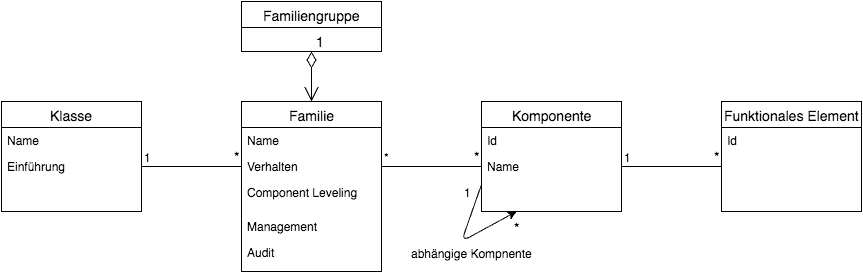
A Supporting Tool For It System Security Specification Evaluation Based On Iso Iec And Iso Iec Springerlink

The Common Criteria Cisa

Bs Iso Iec 1 05

Iso 15 408 E Ciencia Da Informacao E Citi
Ipsj Ixsq Nii Ac Jp Ej Index Php Action Pages View Main Active Action Repository Action Common Download Item Id Item No 1 Attribute Id 1 File No 1 Page Id 13 Block Id 8

Security Standards

Norma Iso Iec Common Criteria Perito Informatico Y Tecnologico Peritoit

Work Products From Iso And Iso Download Table

Tksg 共同準則資訊安全技術評估 Cc Iso Iec 與認證服務
Common Criteria Iso By Thiago Amarante




